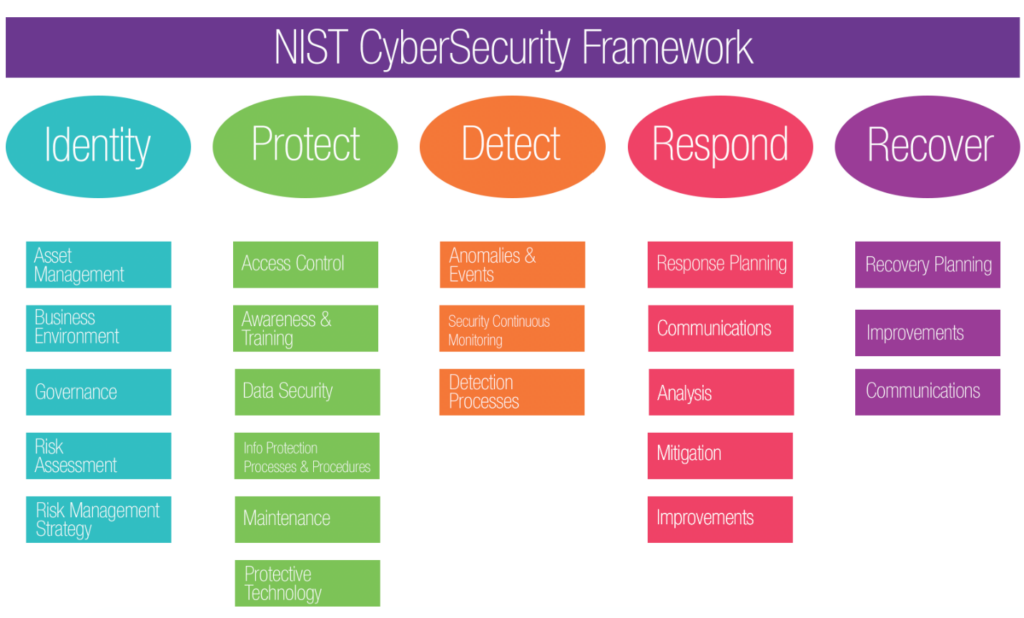
![PDF] Is Information Security Under Control?: Investigating Quality in Information Security Management | Semantic Scholar PDF] Is Information Security Under Control?: Investigating Quality in Information Security Management | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c13a611fc5bd3c2fbb8c8434ed97ce591e71b830/3-Table1-1.png)
PDF] Is Information Security Under Control?: Investigating Quality in Information Security Management | Semantic Scholar

Certified Information Security Manager (CISM) | Professional and Industry | Professional and Continuing Education (PACE) | Lindenwood University

ISO 27001 Annex : A.6 Organization of Information Security | Infosavvy Security and IT Management Training

Information Security Management System : ISO/IEC 27001 Lead Implementer – Mapp Technologies & Services Ltd

Online Certified Information Security Manager (CISM) (Voucher Included) from George Mason University
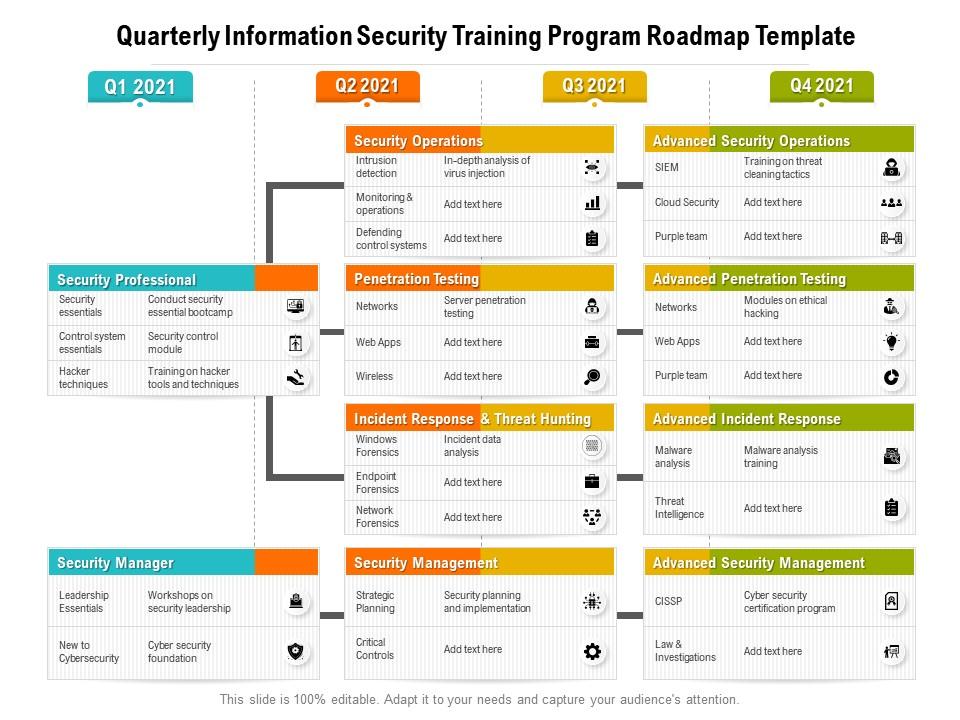
Quarterly Information Security Training Program Roadmap Template | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas